My stuff is Being Given Away all over the Net…what am I going to do???
So, it started with an amazing idea. It was like a light bulb literally appeared over your head, just like in the cartoons. You decided to take your fantastic idea and turn it into a reality, create a new product or develop a new piece of software and sell it to the world online.
You were willing to put in all of the hard work and dedicate yourself. Finally, after all of the sacrifice, your product is complete and ready for sale.
Then it happens. Almost as soon as it is released, you learn that people have got a hold of your idea, and are selling or giving away pirated copies. People who did not have anything to do with the creative process, who did not put the time and perseverance into the development process, have essentially stolen your idea and hard work and are now illegally profiting.
Well, if this has happened to you before, then you know exactly how upsetting it can be. You understand the feeling of being victimized, and the anger that can be associated with that. Theft is theft. It does not matter whether it relates to your car, to your purse or wallet, or to your virtual assets.
Your two best weapons in the fight to keep what is rightfully yours are knowledge and tools that equip you with the “know how” and the ability to go after the people who are siphoning money off the back of your labor.
You need to halt the flow of money going to those pirating your product…because this money should be going into YOUR pockets!!
Understanding the Digital Millennium Copyright Act (DMCA)
Since the internet’s inception, people have been stealing other people’s digital work and re-publishing it illegally for what ever purpose. The Digital Millennium Copyright act was enacted by the US Congress and passed into law on October 12, 1998.
The DMCA helps to fight against these thieves by providing content / software producers as well as online publishers legal ramification should the Copyright Owners find that someone is pirating their virtual assets. The Digital Millennium Copyright Act is intended to stop sites / people that control access to copyright works and increases the penalties for copyright infringement on the internet.
The enactment of the DMCA was extremely good news for the “Good Guys”, and while it helps to minimize and reduce online piracy, the problem of online piracy is rapid and widespread. To put it simply…if you are producing content / software and making it available online (especially if you are selling it), there is an extremely HIGH probability someone has taken your material and is distributing it for free all over the internet or has stolen it, repackaged it and selling it as their own… stealing YOUR profits.
As unfortunate as it is, if you suspect your Virtual Assets have come under attack by online pirates you probably won’t be able to get them all. However, by arming yourself for battle and fighting back you can greatly reduce the availability of your pirated work.

Taking Down the Bad Guys
Once you have determined your work has been pirated and have evidence that Copyright Infringement has taken place, it is then time to go on the offensive. The mission is to focus on the targets, and then act quickly armed with knowledge.
Most of the time you can successfully have your pirated content removed within 48 hours of the correspondence you send. We have actually had sites shut down or temporarily suspended, or pirated download files removed from the net within hours…it can and does happen. However, I always recommend taking a laid back initial approach with some most site’s I find material on. Most of the time an initial email to the site owner that is diplomatic does the job…and in some cases builds a new relationship.
Having the right tools, resources and templates will help cut through all of the BS, and help put you in a better position to take back control of your work and the profits you deserve.
The communication you can send to the Target Website Owners, Hosting Companies and Registrars are called “Takedown Notices”. It’s pretty straightforward. These notices instruct the recipients to remove the Pirated information immediately or possibly face legal ramifications.
IT IS EXTREMELY IMPORTANT that you RESEARCH the suspected Pirate site / location from which your Virtual Assets are being distributed. This is especially important if you are offering an affiliate program where several hundred or more people are actively promoting your product.
There are times when certain affiliates will use keywords, marketing messages such as “Get XYZ Free” just to get folks to click through to their site, but once the visitor arrives a bait and switch happens where the visitor is presented a marketing message which leads to the ultimate sale. (One may not agree that this is the most ethical way of driving traffic, but it’s not illegal. For our purposes right now, these people have not stolen your virtual assets or are distributing them…. we will be covering these Affiliate issues and how to deal with them in another post.)
There are also certain requirements that must be met in order for you to correspond with Suspect Sites and hosting companies. Failure to include the following specific information in your “Takedown Request” regarding pirated content could result in less than favorable results in your fight to have your files removed.
DMCA Infringement Contact Requirements
Notice from Copyright Owner
The first way an OSP can be put on notice is through the copyright holder’s written notification of claimed infringement to the OSP’s designated agent. This must[13] include the following:
(i) A physical or electronic signature of a person authorized to act on behalf of the owner of an exclusive right that is allegedly infringed.
(ii) Identification of the copyrighted work claimed to have been infringed, or, if multiple copyrighted works at a single online site are covered by a single notification, a representative list of such works at that site.
(iii) Identification of the material that is claimed to be infringing or to be the subject of infringing activity and that is to be removed or access to which is to be disabled, and information reasonably sufficient to permit the service provider to locate the material.
(iv) Information reasonably sufficient to permit the service provider to contact the complaining party, such as an address, telephone number, and, if available, an electronic mail address at which the complaining party may be contacted.
(v) A statement that the complaining party has a good faith belief that use of the material in the manner complained of is not authorized by the copyright owner, its agent, or the law.
(vi) A statement that the information in the notification is accurate, and under penalty of perjury, that the complaining party is authorized to act on behalf of the owner of an exclusive right that is allegedly infringed.
See 512(a) and (h) from the above link if the information is not stored on the system of the OSP but is instead on a system connected to the Internet through it, like a home or business computer connected to the Internet. Legal liability may result if access to material is disabled or identity disclosed in this case.
Launch a Super Sonic, Cyber Tomahawk Cruise Missile, straight up the gut…in 4 Easy Steps!
There are existing tools at your disposal that you can use to monitor your online assets, and to help prevent their illegal distribution. There is no doubt that more research and resource tools are available on this topic. but lets try to streamline the process to help the busy marketer. Here’s some of the exact same tools and tactics I use to successfully protect my virtual assets and hard work.
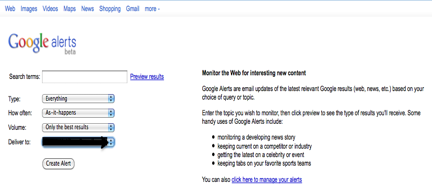
STEP 1 –Google Alerts
One of the very first things you need to do once you have made your product / service available online is to set up a “Google Alert” http://www.google.com/alerts
What is awesome about Google Alerts is that you can set up your alerts to notify you in virtually Real Time. As soon as anyone makes a post that includes the search terms/keywords you have established alerts for, an email will be sent to you. Immediately, you can check to see if there is anything you need to worry about. This is a powerful weapon in fighting the dudes that are ripping you off.
Almost as fast as they post your pirated material you have the ability to be notified, do the research and possibly take action. The faster you know it’s happening…the faster you can pay Karma a visit.
To set up your Google Alert,
1. Enter your search terms | Product Name
2. Select the “Type” you want. You will be able to select various types such as only “News”, “Blogs”, Real time, Video and Discussions,etc…
We always leave ours set to “Everything”.
3. Now you need to select how often you would like to be notified.
We recommend “As-It-Happens”.
4. Next, you will select the “Volume”…this can be either “only the best results” or “everything”.
We recommend “everything”.
5. Finally set the email address where you want the Alerts to be sent.
But you wouldn’t stop there…once you create a Google Alert for your main search term you want to create Multiple Alerts with variations of your keyword term. This would include additional search terms such as FREE (more on this below).
Google Alerts allows you to “Manage” your alert options. You can always re-set the frequency in which you are notified, as well as set different parameters for different alerts, etc. You can sculpt your notification settings based on the specifics of each Google Alert you need to set up. One may be set up for “As-it-Happens” results, where as another alert that you create is set up to only notify you once a week. And so on…
STEP 2 – Expanding Your Investigation,
…Setting up Advanced Surveillance Systems and Targeting Underground Keywords.
Okay….now that you have your Google Alerts all set up you are able to put the search for anyone pirating your material on auto-pilot… sort of like being a cia, ninja bad ass who knows what’s up and can whoop it up. Sure, Google Alerts is going to head out and proactively scour the web for you, but it never hurts to go the extra mile. This is especially true when it comes to ensuring that your property remains yours. So, there is some extra credit legwork that you can do to supplement your auto alerts.
It might seem like overkill, or even duplicated work, but we’ve found that a little extra independent searching for terminology specific to the folks who are swiping material helped us locate their sites.
For example, say the product that we created was named “The Super Proven Method”. We would search for our product name plus some pirate related terms. Be sure you use various search methods, including broad search terms, as well as including your keywords with “Quotation” marks. Some sample searches would look like this:
“The Super Proven Method nulled script”
“The Super Proven Method nulled”
“The Super Proven Method steal”
“Download + nulled scripts The Super Proven Method”
“download The Super Proven Method”
“download The Super Proven Method script”
“The Super Proven Method free download”
“The Super Proven Method share”
There’s a ton more info on this subject, specifically on “Keywords” that are used…but I’m thinking you’ve got the idea 🙂
As your Google Alerts come in, and you independently find sites providing your product illegally, you will probably begin to see the same familiar names and
sites. It is not uncommon to send multiple cease and desist letters to the same sites, hosting companies, etc. Remember, not every site or hosting company that you find providing your material will be doing so knowingly. This must be taken into consideration when you are preparing the templates to be sent out.
So, you have checked out the suspect site and have determined that your materials have in fact been stolen, and are being provided either for sale or for free there. Now you need to move onto the next step.
Step 3 – Recon and Data Collection
….its on like Donkey Kong!
There are a few players involved that you will need to contact to ensure that you have covered everyone. You will be looking for the contact information for the following:
The Site owner – This is pretty self explanatory they are the people / persons who owns the website.
The Registrar – The registrar is an organization that has been accredited by ICANN to register top level domains (TLD’s) – that is, domain names ending in standard extensions such as .com, .org, or .info. The domain registrar is responsible for maintaining domain registration records, for managing domain renewals, and other administrative details. The registrar is responsible for keeping personal contact information, which could be valuable information for you in this process.
The Hosting Company – The hosting company sells space on their web servers to the public. They allow individuals and companies to make their websites available to the public through the World Wide Web.
Making contact with the registrar and/or hosting company could come as a surprise to them, but the site owner should not be too shocked to receive notification from you. In fact, do not be surprised when you receive replies from the hosting company or registrar where they are giving you tips, or pointing you in the right direction. One of the fastest ways to obtain this information is to perform a Whois Search.
To search the WHOIS, choose the option below that corresponds with the extension of your domain name. On the WHOIS search page, enter your domain name and review the results to find the name of your registrar.
- To search for domain names ending in .aero, .arpa, .biz, .com, .coop, .edu, .info, .int, .museum, .net, and .org, visit the InterNIC web site.
- To search for domains ending in .us, visit http://www.whois.us/.
- For domains ending in a two-letter country code, such as .uk or .jp, try Uwhois.com.
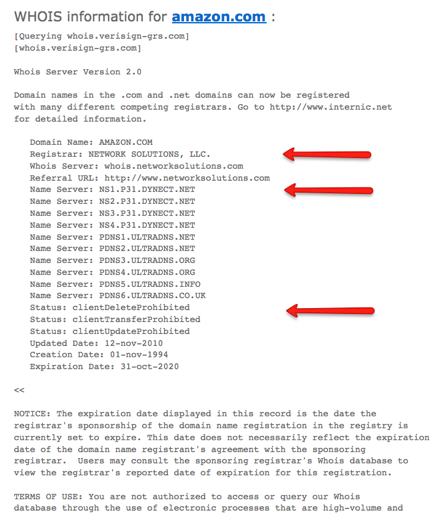
Once you enter the URL and perform the search, WhoIs will provide you with all of the data for that Site URL. Let’s assume that you wanted to find out who Amazon is set up with. Here’s what you would see after you click the Go button:
The information you are looking for can all be found via the Indented Portion of the search result. As you can see above, the first arrow shows the Registrar information, and the second represents the “Nameserver” of the Hosting company. (Sometimes the nameserver can be pointed to another host, in which case the hosting company you contact will usually reply and let you know this. If this happens then it’s up to the Registrar to provide you with the correct information.)
PLEASE NOTE:
-You will notice a series of numbers followed by a URL in the portions that are labeled “NameServer” above. To search and obtain the contact information, you will need to Extract the URL and simply enter into a separate web browser, be directed to the Host and obtain their “Contact Us” link on their website.
Example… The First “NameServer” above labeled
NS1.P31.DYNECT.NET
You would need to Extract the URL and go to www.Dynect.net
The third arrow represents where you can find the site owners information. However, many website/domain owners will often pay extra to set up some kind of Domain Privacy which keeps their information a bit more secure. It’s kinda like paying extra to have your number unlisted in the phone book. You would need to rely on the host or registrar to either supply you the information or make contact with the owner of the suspect website.
The most prudent course of action is to locate their “Contact” information straight from their site via the “Contact Us” link. Do not be surprised if you do not find one, though. It is not often that people who are pirating copyrighted material want to be found so easily. That is why we invariably end up dealing with the hosting company or registrar in these situations.
STEP 4 –Time to Bring the Heat
Contacting the necessary parties
Now that you have identified the people or entities involved in selling your copyrighted work, or are providing it for free, it is time to make contact with them. This is the whole purpose of going through this process – letting the people engaged in distributing your materials know that you know that they are doing it, and that they need to cease and desist immediately.
When we first began contacting people and companies about these situations, we would initially only target the one we felt was the most responsible. That was, of course, most often the website owner. But as we said before, many of the owners of sites where pirated materials are available are not looking to be contacted, and therefore it is not often that they have “contact us” options.
Once we considered it further, it seemed way more sensible to not just contact one or the other, but rather to contact them all at once. We began to send notices to the website owners, the hosting companies and the registrars at the same time. Even if the website owners do not respond, then it is not uncommon for the hosting companies and/or registrar to reply.
Typically, when the hosting company or registrar replies, they often are trying to help you and point you in the right direction, at least. Sometimes they will attach the website owner (and their contact information, intentionally or not) to their reply to your notice. We have found that contacting all parties at once not only saves you time, which is kind of the point of a Quick Attack Package, but also is very effective in achieving your goal – having your materials removed from the offending websites.